Understanding Casebook’s Security and Permissions
Security and permissions in Casebook are designed to protect sensitive client data while allowing your staff to work efficiently and collaboratively. Every agency’s confidentiality needs are different from small community programs to statewide organizations, and Casebook provides flexible tools to ensure the right people have the right level of access at the right time.
🧭 Overview
Human services organizations handle highly sensitive information every day. Casebook helps you maintain client privacy, comply with regulations, and support real-world teamwork through a clear, role-based permissions structure. You can use Casebook’s security settings to:
-
Control who can view, edit, or delete information
-
Reflect how your organization is structured (by team, program, or region)
-
Give supervisors oversight while maintaining staff-level confidentiality
-
Meet privacy and compliance standards confidently
🧩 How It Works
1. Roles — Setting the Foundation
Roles define what each user can do in Casebook, such as view, create, edit, or delete. They apply across all modules such as People, Intake, Engage, and many others.
You can use Casebook’s preconfigured roles or create new ones that match your agency’s structure.
Common Role Examples
|
Role |
Description |
|---|---|
|
Admin |
Access to system configuration settings only. |
|
All Access |
Full access across Casebook for system administrators. |
|
Worker (Intake / Engage / Provider) |
Can view, create, and edit records within assigned areas. |
|
Observer |
View-only access (no edits). |
|
Supervisor |
Full control within their assigned area (view, create, edit, delete). |
|
Reporting Admin / Observer |
Manages who can access or view reports. |
2. Assigning Roles
Roles are managed in Admin → Users. Each user can have more than one role, and Casebook automatically layers their permissions.
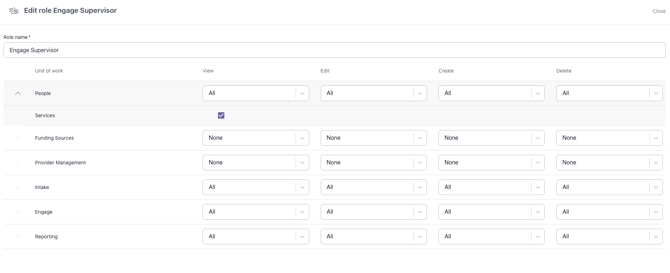
For Example:
“Our Intake Workers need full access to Intake but only read access to Engage.”
Assign Intake Supervisor and Engage Observer roles.
This setup keeps collaboration open where it’s needed and restricted where it’s not.
3. Record-Level Permissions — Access Lists
For programs that handle confidential client data, Casebook lets you control access at the record level. Each record (such as a Case or Intake Report) has an Access panel that shows who can view or edit it. You can manage this in two ways:
From a Record
-
Open a Case, Intake, or Person record.
-
Click Access on the right-hand side.
-
Add or remove users or teams as needed.
From a Workload View
-
Go to Engage, Intake, or Providers.
-
Select multiple records using the checkboxes.
-
Click Bulk Update Access to manage visibility for several at once.
Deny Lists — Adding Extra Privacy Control
While access lists grant visibility, Deny Lists restrict it. A Deny List removes access to specific records even for users or teams who would normally have permission through their role or team membership. This gives administrators an added layer of privacy control without changing the overall permission structure.
Common Uses for Deny Lists:
-
Restricting a single record with highly sensitive client information.
-
Separating visibility between specialized teams (for example, Victim Services vs. Crisis Response).
-
Temporarily limiting access during an internal review or investigation.
Best Practice:
Use Deny Lists sparingly. They’re designed for exceptions that require additional confidentiality, not as your primary way to manage permissions.
🧠 Think of a Deny List as an extra layer of security for special cases that need tighter protection
4. Automatic Security Logic
Casebook automatically adds the right users to access lists to reduce setup time and ensure consistency:
-
The creator of a record automatically gains access.
-
Any assignees are automatically included.
-
The team of an assignee is also added automatically.
🧠 Permissions follow your real-world workflows, so data stays protected and staff stay productive.
5. Teams — Scaling Security Easily
Teams help you manage access for groups of users in a consistent and scalable way. When a team member creates or is assigned a record:
-
Their entire team gains access automatically.
-
Supervisors can see the full scope of their team’s work.
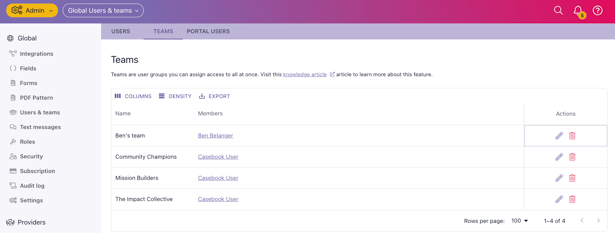
For Example:
A multi-county agency uses “Central Office” and “East Region” teams.
Staff in each region automatically share access within their group, while remaining fully secure from other programs.
🧠 Teams help organizations scale securely without exposing unnecessary data.
6. Inherited Permissions — Supporting Complete Workflows
When a user can view a Case or Intake, Casebook automatically includes limited, relevant details about linked People or Providers.
For example:
A worker viewing a case can see key identifiers for the people involved, even without full access to their entire profile.
This ensures staff have the information needed to act, while still maintaining strong privacy boundaries.
💼 Security Models for Different Needs
|
Setup Type |
Description |
Best For |
|---|---|---|
|
Open Access |
All staff can view and edit records. |
Programs emphasizing transparency, like outreach or resource navigation. |
|
My Work Only |
Staff see only what they’re directly assigned. |
Casework where client confidentiality is essential. |
|
Team-Based Access |
Teams share visibility within their own group only. |
Multi-program or regional agencies. |
|
Restricted Access |
Access is granted per record or case. |
Programs with strict privacy requirements (e.g., behavioral health or domestic violence). |
💡 When to Adjust Permissions
Adjust security settings when your organization needs to:
-
Protect client confidentiality and sensitive information
-
Limit visibility between programs or departments
-
Maintain compliance with local or federal privacy laws
-
Prevent over-sharing between teams or contractors
🧠 Best Practices
-
Start with roles. Use Casebook’s default roles as your foundation.
-
Use teams for efficiency. They simplify large-scale access management.
-
Review permissions regularly. Confirm that staff only see what’s relevant to their role.
-
Rely on automation. Casebook automatically handles common access patterns.
❓FAQs
Q: Will staff automatically have access to their assigned cases?
Yes. Casebook automatically adds the assigned user and their team to the record’s access list.
Q: Can supervisors see what their team is working on?
Yes. Supervisors automatically see their team’s assigned cases when team access is enabled.
Q: How can I let two programs collaborate on a shared client?
Add users or teams from another program directly to the case’s access list.
Q: Do I have to update access manually each time?
No. Casebook automates most access updates for common workflows. Manual edits are only needed for exceptions.
📘 Related Articles
Use these guides to dive deeper into how permissions work across Casebook:
-
Privacy: How to set up User Roles and Permissions to protect your Client data
-
Permissions for Engage: Assign and Control Access with Precision
-
Permissions for Intake Reports: Control Access with Confidence
-
Privacy: How to set up User Roles and Permissions to protect your Client data
📞 Need Help?
If you're unsure how to update roles, build teams, or apply access changes, contact our Support Team. We're happy to help.
.png?width=1286&height=255&name=logo-raspberry%20(1).png)